The arguments of critics of the iPhone abound, among them, the impression given by the iPhone to users to be caught in the shackles of Apple’s user restrictions. Indeed, the iPhone, and other iDevices, are sold that way for marketing and technical reasons, so the degree of manipulation and customization left to the user is reduced to its simplest expression, which does not suit everyone. Thus, when Jailbreak, a computer hack which could bypass the limitations installed by Apple was released in 2007, by a hacker named George Hotz, (also known as Geohot), he and his exploit became famous overnight. Moreover, because a complicated exclusivity deal the iPhone, at the beginning was only available over AT&Ts networks yet Hotz got one to work on T-Mobile’s network after buying an iPhone the day it came out. Using a complicated method (it was necessary to open the iPhone and make welds) he was able to unlock an iPhone for the first time. Once his exploit became more widely known, other, more sophisticated software manipulations became available as other hackers tries to emulate him (as we shall see below), although Geohot is still considered to be the father of the jailbreak.
So Jailbreaking is a process for devices running the mobile operating system of Apple, iOS (Ipad, iPhone, iPod touch) to get full access, to unlock all the features of the system operation and to bypass the restrictions imposed by Apple. Once unlocked, users can download new applications, extensions and themes that are not offered on the official application store from Apple, the AppStore, via installers. An unlocked iPhone or iPod touch can still use the App Store, iTunes and all other basic functions of the device. The jailbreak is similar to “rooting” for an Android phone.
Obviously the problem with Hotz’s method was that it was necessary to modify the internal components of the iPhone. So, other developers worked on a way to unlock the iPhone by modifying only the software. Some companies were also looking for this solution and promised to sell the method, but found nothing. Until September 11, 2007, when the company iPhone SIM Free found a method and announced it would be sold for $99. Shocked by this announcement, a team of developers, the Dev Team, decided to release their own method for free. The day the company iPhone SIM Free released its method, the Dev Team released their own. Shortly after, the Dev Team released a jailbreak tool for latest version of iOS (1.1.1 at the time).
In March 2008, Cydia, named after a worm feeding on apple, was released although the AppStore still didn’t exist. Cydia is an unofficial iOS application developed by Jay Ryan Freeman, aka Saurik, open source, and providing an access to applications not digitally signed by Apple. The announcement of the AppStore arrived four days later. To date, many easy-to-use methods to jailbreak iPhones are available on the internet, virtually all Apple iOS version can now be jailbroken .
The main interest of this manipulation is to install themes on the springboard, tweaks, to modify the use of the buttons, and install unofficial third party applications. These applications and themes can be downloaded platforms other than the AppStore such as Cydia and Icy. Unlocking also allows the users to change the user interface elements such as icons, unlock the carrier, share internet connectivity, browse the device via SSH.
However, the jailbreaking has some risks. Viruses exist and can gain access through installing unofficial third party applications, particularly if they do not come from reliable sources. They will probably not physically damage the unit but could affect the operating system and be a security issue (sensitive data like passwords, for example, could be misused for malicious purposes). The first iPhone virus appeared in November 2009 and was created by Ashley Towns, an Australian student aged 21. He says he aims to raise awareness of the problems security
« When people jailbreak Their phone, it allows to install a service on Their phone Called SSH, generally you should always change your password After setting up on the iPhone, all iPhones use the same password. This virus pretty much exploits people’s laziness to Change their password. »(Indeed, when SSH is installed on jailbroken iPhones, the default log name is « root » and the default password is « alpine »). – Ashley Towns, ABC News.
This virus exploited the general trend does not change the SSH password by default. He just put in the background of a phone photo of Rick Astley. Another example: November 22, 2009, F-Secure reports the presence in the Netherlands a new worm compromising banking transactions made from unlocked iPhones.
With the jailbreak also comes the problem of piracy. According to Pinch Media Institute, all iPhone apps can be found on peer-to-peer networks and file sharing websites, they also claim that 4 million units, out of 50 million iPhone and iPod Touch, contain applications pirated. Hackers have created applications to override the security of Apple at the application level. It is then possible to install applications illegally, without paying. The jailbreak then moves away from its first goal. That is why some famous hackers such as « i0n1c » want to block the IOS pirated applications with the jailbreak for the new iOS 5. In China, the number of unlocked devices is over 35%, whereas it is less than 5% in Japan. Figures also indicate that the rate of jailbroken iPhone in the U.S. is 5% and 8% in France. Moreover, although the tools to unlock iOS terminals have reached a certain maturity, the operation can sometimes lead to blockage of the terminal and damage the operating system.
From a legal point of view jailbreak is not illegal. The DCMA decided in July 26, 2010 to allow iPhone owners to bypass the lock installed by Apple to download applications that have not been approved by the company. The unlock is then made legal in order to use the iPhone on another network than AT & T, or to allow to use applications not approved by Apple but is allowed only in these cases. Jailbreaking for hacking applications, however, is prohibited by law.
In February 2009 Apple exposed its official position towards the jailbreak: « Techniques of jailbreaking, widely spread, involve unauthorized modification of the boot loader and operating system » and says this “leads to a violation of copyright affixed to these programs.” Apple said that this operation will compromise the warranty of the device. Apple fights unlock in software vulnerabilities by correcting previously used to circumvent the restrictions of the system.
Here is a few selection of useful applications for jailbroken iDevices.
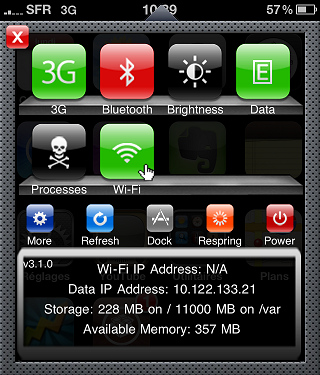
Sbsettings
Allows very fast action such as mute / unmute the Wi-Fi or Bluetooth, restart your iPhone or quit applications. To access this panel stock, simply sweep your finger up the screen.
Winterboard
The application is used to change the theme of your springboard;
you can upload thousands of themes on Cydia or create your own.

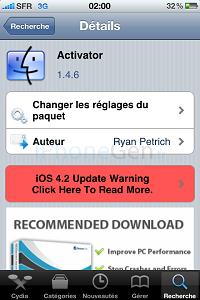
Activator
It will allow you to assign to any predefined combination the opening of an application,
or even a feature of your device.
QuickLock (OS3.x) / QuickLock 2 (iOS4.x)
Allows you to lock your device. Simply press the QuickLock icon on the SpringBoard to have your phone locked and the screen turned off. Useful for those who have damaged their power button or for those who would take care of it.
Xyflash
A powerful media player, you can upload any video from your computer without converting it before and read it on your device.
Pdanet
An application that allows you to share your mobile internet connectivity with other device such as a computer. Useful when you need internet and you are away from a Wi-Fi hotspot.
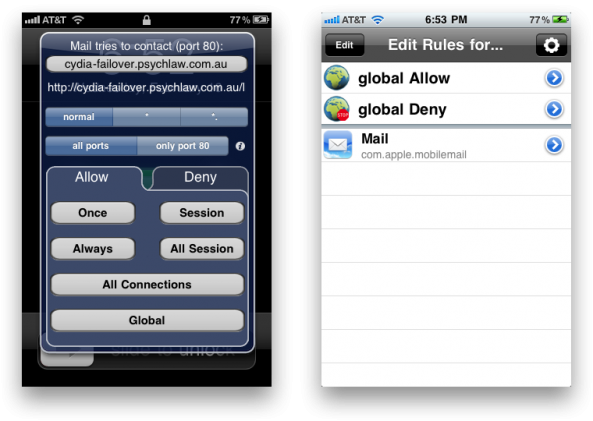
Ip firewall
A firewall for your iPhone. For now Ip Firewall is the only application that protects you from unwanted internet connection. You can use it to prevent third party internet applications to collect private information.
Sources:
- Fred von Lohmann, « Apple Says iPhone Jailbreaking is Illegal [archive] », Electronic Frontier Foundation, 12 Febuary 2009.
- Mike Keller (February 13, 2012). « Geek 101: What Is Jailbreaking? ».
- Geek Tech. PCWorld. Retrieved February 15, 2012.Leander Kahney (July 26, 2010). « Apple’s Official Response To DMCA Jailbreak Exemption: It Voids Your Warranty ».
- Cult Of Mac. Retrieved October 26, 2011.Ellis Hamburger (May 3, 2011). « The Truth About Jailbreaking Your iPhone: The 5 Biggest Drawbacks »
- Brennon Slattery (August 3, 2010). « 5 Reasons to Jailbreak Your iPhone – and 5 Reasons Not »
- Tim Wu (October 4, 2007). « The iPhone Freedom Fighters »
- John Paul Titlow (January 20, 2012). « Now You Can Jailbreak Your iPhone 4S and iPad 2 »
